Rule Page
Open the Rule's Page
- From the Security Rules list, in the Rule Summary column, click a Rule number.
Rule Hit Counts
Security Manager tracks how many times a rule is used in a 24-hour period. This data is stored in increments of 30, 90, 180 or 365 Days.
On the Security Rules page, click Hit Counts and select the number of days to view: 30, 90, 180 or 365 Days.
Rule Configuration
This is the same information from the All Security Rules list table. Click any linked rule information to open its related page.
Rules KPIs
- Rule Cumulative Severity—the combined total severity of all rules in a policy
- Control Failures—a count of the total number of controls failing the rule that occurred the last time an assessment ran for the selected device
- Configuration Changes—a count of the number of rule configuration changes in the last seven days
- Hits—a count of the total number of hits on this rule in the last 30 days
- Rule Risk Score—the ratio of vulnerabilities not exposed by this rule to total number of potential vulnerabilities, adjusted by Asset Value and effect multipliers
Rules Widgets
- Rule Usage—a 30-day history of the rule's usage
- Control Failures—failed controls by severity assigned to the control at creation
- Vulnerabilities Not Exposed by this Rule—list of the number of Root, User, DoS and Other vulnerabilities not exposed by this rule
- Vulnerabilities Exposed by this Rule—list of the number Root, User, DoS and Other vulnerabilities exposed by this rule
- Change History—the top 20 changes made to this rule
- Rule Documentation—the meta-data that explains the rule
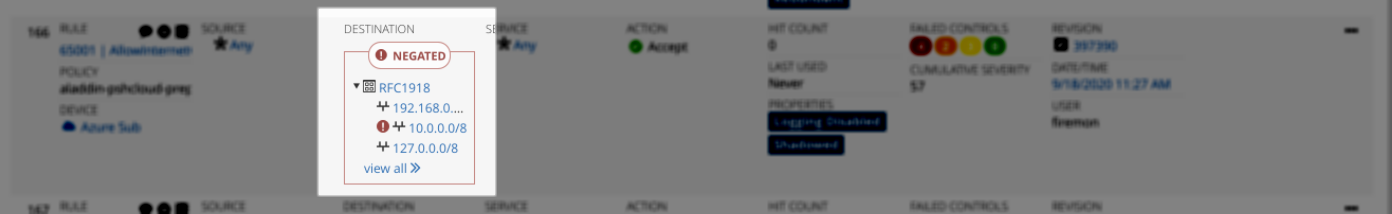
Negated Objects
All objects within a security rule on source , destination or service can be negated. Devices support both regular and negated objects in a rule. Security Manager supports the display of these negated objects within the UI.