Prechange Assessment KPIs and Widgets
When you clicked Show for a change in the Change Plan: Projected Device Impact table, these are the KPIs and widgets that open.
KPIs
-
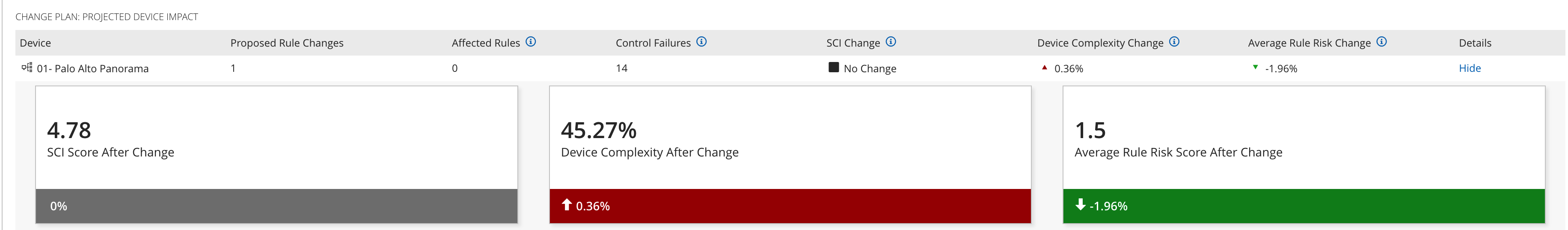
SCI Score After Change: Each proposed rule change in a requirement on a ticket may impact the Security Concern Index (SCI), which is a metric that compares the ratio of failed control severity in a network to the total control severity a network. You can use the SCI to analyze whether you have a relatively high or low number of failed controls. Each proposed rule change will either raise, lower, or have no effect on the SCI score. The SCI Change column in the Change Plan: Projected Device Impact table tells you whether the proposed rule change will raise, lower, or have no effect on the SCI score. The SCI Score After Change KPI tells you what the SCI for your network would be after implementing a proposed rule change.
SCI score changes cannot be calculated for general (non-rule) changes or Delete Rule tasks. For those changes, the SCI Score field will read "Not Applicable."
-
Device Complexity After Change: Each proposed rule change in a requirement on a ticket may impact the device complexity, which is a percentage that measures the intricacy of a device's firewall rule configuration. The higher the device complexity percentage, the greater the risk of a configuration error.
Device complexity changes cannot be calculated for general (non-rule) changes or Delete Rule tasks. For those changes, the Device Complexity Change field will read "Not Applicable."
-
Average Rule Risk Change:The score is calculated by taking the average of all of the proposed Rule Risk Scores for the device.
The bottom of each KPI has a color-coded metric:
-
Green if the number went down
-
Red if the number went up
-
Grey if no changes or no data available
Widgets
Control Failures for Planned Changes
| Value | Description |
|---|---|
| Severity |
The severity level of the control failure.
|
| Control Code | The classification code that was assigned to the control when it was created. |
| Control Name | The name of the control. |
| Related Assessment | The assessment used by the control. |
| Remediation Instructions | Instructions that were entered when the control was created in the Administration application will be seen here. |
| Indicator | Level | Range |
|---|---|---|

|
Low | Between 0 and 2 (inclusive) (0-2) |

|
Medium | Greater than 2 and less than or equal to 5 (3-5) |

|
High | Greater than 5 and less than or equal to 7 (5-7) |

|
Critical | Greater than 7 (8-9) |
Control Codes
There are seven available control classification codes that are derived from the security control identifiers found in the National Institute of Standards and Technology (NIST) 800-53 publication. Classification codes are automatically assigned to a control when it was created in the Administration application. The following list defines the classification codes.
| Code | Classification |
|---|---|
| AC | Access Control |
| AU | Audit and Accountability |
| FM | Federation Manager |
| IA | Identification and Authentication |
| RA | Risk Assessment |
| SC | System and Communications Protection |
| UD | User Defined |
Change Details
| Value | Description |
|---|---|
| Change ID | The rule number or object type. |
| Policy | The policy associated to the rule change. |
| Proposed Change | The change to be implemented. |
| Details | Click Show to view detailed information about the change. |